An Introduction To SolarWinds Orion’s Device Configuration Compliance Reporting
SolarWinds® Network Configuration Manager (NCM) delivers a continuous auditing tool to automate the configuration compliance checks, within its common web UI, alongside the health, performance and utilisation monitoring function it is known so well for. When the configuration compliance feature is configured, it will run daily search on device configurations backups to spot noncompliant setting and make you aware of configuration divergences in the form of Policy Report.
Having such functionality provided alongside the monitoring data allows for very quick impact visibility and identification if configuration issues are the cause of the status or performance issue the monitoring metrics indicate, which we all know is a very common circumstance.
Orion® NCM comes with 169 Compliance Reports pre-built across common compliance frameworks, such as PCI, SoX, as well as vendor ‘best practice’ based reports, this is a great starting point. However, I always discuss with our clients the importance of creating your own company policy reports in NCM. Every organisation should have a common configuration definition across similar devices, for example if you run devices from a few vendors, it is likely you will have only a few network operating systems to create reports for. Knowing all your devices are correctly configured to support a common authentication definition, or sending standard logging to a specific destination is just a couple of examples of the importance of validating configuration definition is in place across all of your device infrastructure.
Policy Reports can be displayed on SolarWinds Orion GUI or sent by email on schedule. Each Policy Report includes one or more policies, while each Policy also includes one or more Rules.
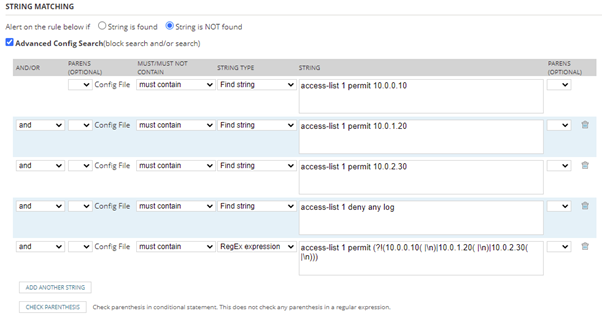
A rule defines a condition that must or must not exist. The condition can be a string search, or a Regex pattern, or even a mix of a few string searches and Regex patterns.
When set condition in Rule, multiple config searches can be used to cater for all situations. For example, when checking ACL rules, we can search if all standard ACL rules exist. At the same time, config searches can be created to find out if there is any non-standard ACL defined. This ability to look for configuration that exists that shouldn’t is a powerful and often missed capability, which extends the benefit this feature provides.
Case Study
Take the following standard ACL rules, which we want to validate are in the configuration of all of our Cisco devices:
[code]access-list 1 permit 10.0.0.10
access-list 1 permit 10.0.1.20
access-list 1 permit 10.0.2.30
access-list 1 deny any log[/code]
Within the Rule definition, we have provided below the definition to confirm that the above configuration exists on our Cisco devices, which the NCM Policy Report will flag any uncompliant devices, so you can review and resolve.
A policy groups related rules, and specifies which nodes the rules apply to. Dynamic selection of nodes is also possible. For example:
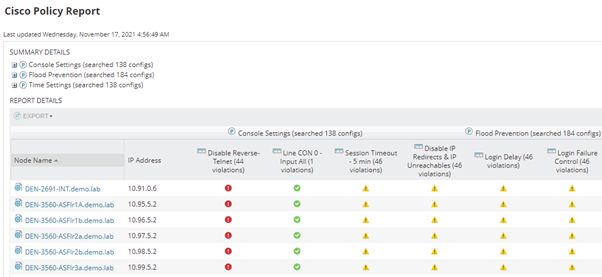
A policy report groups together multiple policies. With regular configuration backups being taken from the devices by NCM, with real time and once a day our recommendation, the Compliance Report feature scans this latest device configuration and matches against all Rules looking for any new compliance breaches. Colour coded icons are used in the report represent pass or different level of violation. Hovering over each violation icon displays details of the violation, and what rule was violated.
Top Tip: Create a new report and populate it will existing rules and add your own rules to complete your report. The out of the box rules are a fabulous starting point to build something aligned to how you want to have your network configured.
Product Trial: SolarWinds Network Configuration Manager

Jin Wu
Senior SolarWinds Field Engineer
Jin is a Senior SolarWinds Field Engineer at Prosperon Networks. As a SolarWinds Engineer for over three years, Jin has helped hundreds of customers meet their IT monitoring requirements with SolarWinds.
Product Trial: SolarWinds Network Configuration Manager
Related Insights From The Prosperon Blog
The Critical Role Of The Trusted Advisor In NetOps
Before there was “Network Operations” there were networks. Networks grew out of a need for connecting one box to another, sharing printers, and for more advanced users,...
Webinar On-Demand: Beyond Monitoring – Introducing SolarWinds Observability Platform
In this webinar, you will discover how SolarWinds® is evolving to deliver complete infrastructure visibility. This webinar examines how to extend visibility across your IT...
Webinar On-Demand: Extend your monitoring visibility beyond SolarWinds Network Performance Monitor
In this webinar, you will discover how to extend your monitoring visibility beyond the network with SolarWinds® Server & Application Monitor, Netflow Traffic Analyser,...